REVIEW ICO PEER MOUNTAIN - PEERMOUNTAIN.COM
TRUST IN THE DIGITAL ECONOMY
Peer Mountain is the cross blockchain protocol that
connects self sovereign ID holders with businesses, enabling commerce at scale.
The only decentralized identity and compliance
ecosystem that puts people in control of their protected personal information,
delivers instant cost effective risk reduction to businesses and pays ID
verifiers for their trustworthiness.
Peer Mountain
goes beyond providing users with ownership and control over their
cryptographically secure identities. It is an end-to-end application ecosystem
that facilitates secure commerce and exchange of digital and physical services.

Helping businesses engage and protect
their customers

Peer Mountain is making blockchain commerce a
reality. Using a forms-based architecture, businesses can seamlessly transact
data with self-sovereign identity (SSID) solutions to improve the security and
efficiency of their commercial operations.
Patent-pending
Peerchain™ technology encrypts and decentralizes data in
all its states, providing businesses with automated regulatory data protection compliance and push-button
auditing.
- Automated onboarding increases operational efficiency
- Swift, secure ID verification improves customer experience
- Blockchain audit trail provides push-button auditing and instant regulatory data protection compliance
- Decentralized data operations reduce risk of data breaches and hacking
Peer
Mountain is always FREE for individuals. They simply need to download the
mobile app and set up their profile to start enjoying the benefits of
membership in Peer Mountain’s ecosystem of identity, trust, and commerce.
Solving the digital identity crisis

Official identity
Information can be stolen from organizations that centralize the data they collect.
Information can be stolen from organizations that centralize the data they collect.
Personal identity
Details are commodities that can be purchased for potentially corrupt purposes.
Details are commodities that can be purchased for potentially corrupt purposes.
One Digital Identity
Peer Mountain facilitates identity consolidation through an intuitive mobile application, providing the peace of mind that comes with comprehensive, blockchain-based identity protection.
Peer Mountain facilitates identity consolidation through an intuitive mobile application, providing the peace of mind that comes with comprehensive, blockchain-based identity protection.
This is Peer Mountain
Peer Mountain Token
(PMTN)

Utility token fueling the Peerchain protocol
Verifiers earn PMTN based on trustworthiness
Attestations become new revenue streams for
institutions
Mobile app

App in Alpha
v.1 release in Fall
Co-build with major financial institution
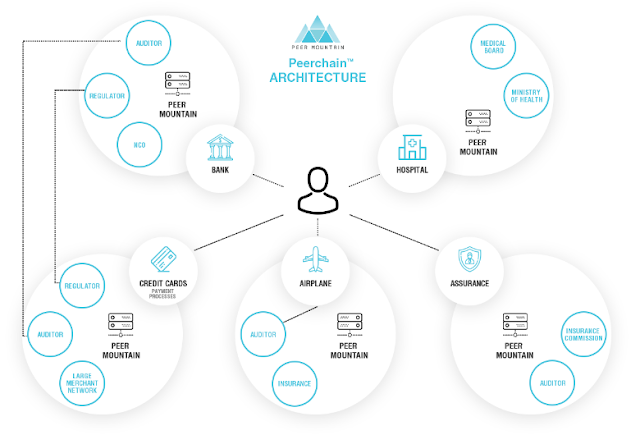
Peerchain™

A seamless P2P blockchain network made up of Peer
Mountain instances; that is, blocks of nodes across parties that require trust.
Practically Invulnerable to Fraud and Theft
Control your data in a distributed system that makes
hacking unfeasible.
Scalable Beyond Today’s Blockchain Capacity
Segment services across Peer Mountain deployments
securely and transparently.
Granular Control
Only share and validate encrypted data according to
transaction requirements
Truly Peer-to-Peer
Peer Mountain serves consumers who want
self-sovereign identity, service providers who need continuous,
reliable compliance, and trust providers offering validation services who
need trust interoperability and portability.
Auditable and Accountable
Gain assurance
TECHNOLOGY
We have also filed
trademarks for the Peer Mountain and Peerchain™ brands with EUIPO trade
mark numbers 017282931 and 017350182, respectively. It is our intent to release
the Peer Mountain client SDK for Android and iOS as open source, and to
open-source the Peer Mountain Attestation Engine SDK. It is also our intent to
submit the Peerchain™Protocol for RFC in order to develop an open standard that
can be used as widely as possible in any economic context.
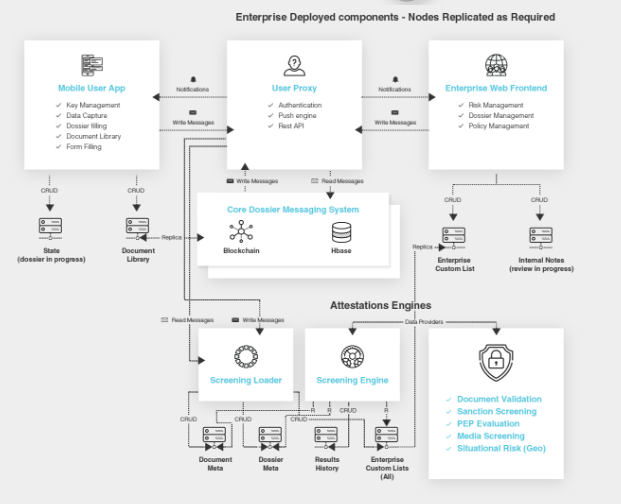
Peerchain™ Protocol

Every operation in Peer
Mountain is defined by a message type. These messages are wrapped in an
envelope that provides the basic common information about all operations. The
messages themselves contain the specifics about their respective operation.
Messages that alter the state of the system are hashed and timestamped in an
immutable blockchain layer.
Service providers, or
other external entities (e.g. regulators), may run blockchain nodes without
necessarily running Message/Object storage nodes.
Only the message
identifier and hashes related to the content of the message is stored on the
blockchain layer. All other information is kept in a high-performance database.
Cross-Chain Compatibility
Different blockchains are not compatible
across chains, and are incapable of handling cross-chain transactions across
multiple chain instances.
Peer
Mountain overcomes this challenge. Chains and storage make up the operating
layer of each instance. The patent-pending PeerchainTMProtocol
then enables Peer Mountain users to communicate across instances, so they can
transmit digital assets across chains. In addition, digital signatures recorded
in one instance remain legally binding throughout the Peerchain™
Efficient,
Transparent Transactions

Latency in communication between a
blockchain’s nodes nodes as it establishes consensus across the chain limits
its transaction capacity. This means that blockchains seem unable to process
transactions at the speed required for large-scale transaction processing
systems.
We’ve taken an innovative approach to
addressing this limitation. We believe that a blockchain does not need to
operate globally on every possible node. Instead, Peerchains™can co-exist and work in harmony, each
focusing on a part of the larger ecology of trust.
Each
Peer Mountain instance operates a Peerchain™ that
we can deploy to a service provider, their regulator, their auditors, and any
appropriate industry watchdog or consumer protection group. Anyone wishing to
review the integrity of the chain can access a publicly available chain
explorer.
Peerchain™ Technology
Clients see Peer Mountain
instances transparently.
Attestations are portable
across instances.
Instances are deployed by service providers operating in regulated
industries.
Storage
Blockchains are not meant
to store large amounts of data, which makes perfect sense: the smaller the data
structures, the more efficient the blockchain.
Peer
Mountain chains store hashes that refer to, and retrieve, encrypted information
held in off-chain storage. A Peer Mountain instance can store encrypted objects
on Storj, IPFS, HDFS, TahoeFS, Amazon S3, or any other available storage
solution that delivers consistent, high-level read/write performance.
High
Scalability

Due to their consensus mechanism,
blockchains require a higher data throughput. However, blockchains don’t have
the capacity to handle large quantities of transactions simultaneously.
Peer Mountain allows for secure and
transparent service segmentation across blockchain deployments. This means an
organization can deploy services that require a high volume of real-time
transactions on a dedicated Peer Mountain blockchain, while deploying the rest
of their services on a common Peer Mountain blockchain.
For example, a bank could run separate
instances for current accounts, specific types of credit cards, and auto loans.
This setup splits the transaction volume across instances, enabling the bank to
achieve higher cross-service data throughput, as well as cross-instance data
compatibility. This means the bank can use information from a customer’s credit
card dossier in the auto loan and current accounts instances.
Use Cases

As
Peer Mountain is an open protocol, businesses can apply it to any use case
where they need personal information from customers, and need to verify their
identities.
A driver can
complete and submit a car rental form with a few taps and instantly receive
digital keys to their rental in their PM profile.
The car rental agency gets
ID verification, and all other required information, without actually seeing
any data.
The driver can use multiple ID verifiers to complete complex
forms, then give the car rental agency access to the verifications – never
detailed personal information.
An ecosystem of identity,
trust, and commerce

Peer
Mountain sits at the intersection of
- Businesses who need continuous, reliable data protection compliance and efficient service delivery
- People who want self-sovereign identity
- ID verifiers seeking new revenue streams.
Peer
Mountain connects all three groups as the facilitating technology for a
versatile trust ecosystem.
Businesses
can speed up, and protect form-reliant processes with an enterprise-driven
solution that is fully compatible with other SSID solutions.
Peerchain™ unlocks
blockchain’s full potential

Patent-pending
PeerchainTM architecture solves some of the key issues of this rapidly evolving
technology, offering a wealth of benefits that include:
Easy scalability
Anyone can run as many local instances as they wish.
Anyone can run as many local instances as they wish.
Maximum versatility
Blockchain-agnostic architecture ensures that Peer Mountain instances function seamlessly on any blockchain platform.
Blockchain-agnostic architecture ensures that Peer Mountain instances function seamlessly on any blockchain platform.
New revenue streams
Anyone can be an ID verifier and earn PMTN whenever their verifications are used in the Peer Mountain ecosystem.
Anyone can be an ID verifier and earn PMTN whenever their verifications are used in the Peer Mountain ecosystem.
Instant data
protection compliance
People share only the information they want to share, and not the data itself, but verifications based on zero-knowledge proof.
People share only the information they want to share, and not the data itself, but verifications based on zero-knowledge proof.
Increased business
opportunities
PeerchainTM offers access to new international markets in the blockchain sphere.
PeerchainTM offers access to new international markets in the blockchain sphere.
The Peer Mountain Token (PMTN)

The PMTN is the utility token for measuring the
value of trust within Peer Mountain’s peer-to-peer ecosystem. Token holders can
use it to pay for ID verifications in the Peer Mountain network.
With
millions of trust-based transactions occurring daily, the demand for PMTN is
likely to grow. Due to its finite supply, the token is also likely to rise in
value as transaction velocity and utilization increases.
Designed
using Ethereum, the ERC-20 compatible PMTN is cross-chain compatible. Holders
can exchange or use it across multiple Peer Mountain instances, with the
Ethereum mainnet acting as a transfer rail.
Get
bonus PMTN in the early rounds of the ICO
Get 30% bonus PMTN the 1st round of our transparent,
fair, and compliant ICO – sign up now to get on the whitelist!
OUR TEAM
Frequently Asked Questions
Why is there conflicting information
on your Bitcointalk thread and the information about your token sale on your
website?
We have recently
partnered with award winning ICO advisory TokenMarket, and together we have
come to the conclusion that we would like to make some adjustments to our Token
event. This will focus on better rewarding the community and contributors which
will in turn improve the project. We are thus making these amendments and will
update all very shortly via our channels.
How is the Peer Mountain token sale
financed?
Investment to date is
from KYC3 and some of the advisors. All stakeholders are represented in the
team/advisor pages on the site.
Will the Peer Mountain project be
reviewed and/or open sourced?
The mobile SDK and the Attestation Engine SDK will
both be open sourced.
The whole system (code,
crypto and deployment architecture) will be reviewed before putting the first
production pliot in place with our Swiss partner.
Are you planning to add any more team
members or advisors in the near future?
We are hiring more
developers and community manager. We are considering an Ambassador Advisor
program for community outreach.
How safe is it to upload identity
documents to your website and app?
The Peer Mountain website and mobile app will handle
and protect ID data in accordance with data protection laws in effect.
Is Peer Mountain using a reputable
3rd party for KYC verification?
Peer Mountain is using KYC3 for KYC
verification.
INFORMATION
Web: https://www.peermountain.com/
Twitter: https://twitter.com/PeerMountain
Facebook: https://www.facebook.com/Peer-Mountain-489107644789749/
Linkedin: https://www.linkedin.com/company/27008860/
Telegram: https://t.me/peermountain
Reddit: https://www.reddit.com/r/PeerMountain/
Steemit: https://steemit.com/@peermountain
Author: Vincent
Admin group Airdrop & ICO: https://www.facebook.com/groups/174689159952121/
My bitcointalk: https://bitcointalk.org/index.php?action=profile;u=1190609
Myetherwallet: 0x5A68BedC4609AB68a2f14CD610B06786983Fe804
Myetherwallet: 0x5A68BedC4609AB68a2f14CD610B06786983Fe804











Nhận xét
Đăng nhận xét